The Kromtech Security Center has identified over 4,000 instances of ElasticSearch servers that are hosting files specific to two strains of POS (Point of Sale) malware — AlinaPOS and JackPOS.
Researchers discovered these exposed ElasticSearch servers last week during routine scans. Intrigued by their initial discovery, the Kromtech team used Shodan to identify more than 15,000 ElasticSearch instances that were left exposed online without any form of authentification.
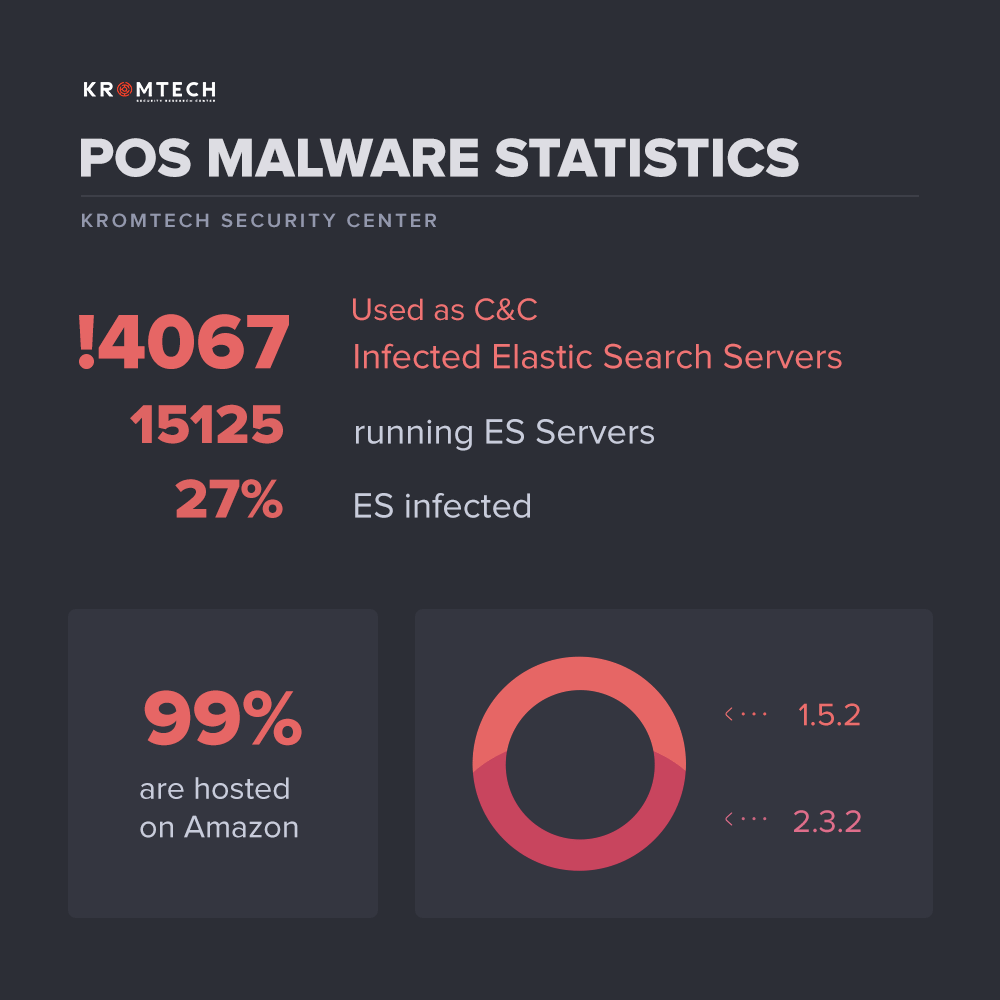
Of these 15,000 servers, Kromtech says that over 4,000 are hosting files specific to the command and control (C&C) infrastructure of AlinaPOS and JackPOS.
That's around 27% of all exposed ElasticSearch instances. The number is way too large to be just a coincidence, especially since the servers hosted mainly POS malware control panels.
Unwittingly, Kromtech researchers appear to have stumbled upon a well-kept secret in the POS malware cybercriminal community — using ElasticSearch servers to hide C&C servers.
99% of infected servers hosted on Amazon AWS
An analysis by the Kromtech team also revealed that 99% of the POS malware-infected ElasticSearch servers were hosted on Amazon's AWS service.
"Why Amazon? Because on Amazon Web Services you can get a free t2 micro (EC2) instance with up to 10 Gb of disk space," Bob Diachenko, Kromtech's Chief Communication Officer explained. "At the same time, t2 micro allows to set up only versions ES 1.5.2 and 2.3.2."
Not surprisingly, 52% of 4,000 infected servers ran ElasticSearch 1.5.2, and 47% ran ElasticSearch 2.3.2.
File timestamps revealed infections going back to 2016 and as recently as August 2016.
In addition, researchers found different packages of the same POS malware and evidence suggesting that servers were infected multiple times over.
Furthermore, Diachencko tells Bleeping computer that both AlinaPOS and JackPOS groups seem to shifted their focus towards discovering vulnerable ElasticSearch servers.
"They are now automatically targeting/scanning for ElasticSearch Amazon instances with no authentication in place," Diachenko told Bleeping Computer in a private conversation.
"A week ago we have deployed several honeypots with emulated ES instance and logged several scan attempts coming from China and [a] blacklisted IP trying to 'get in touch' with our server and possibly install malware," the expert told us.
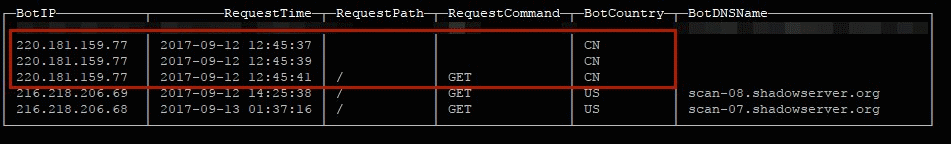
Notifications being sent out to some of the affected companies
"We have sent notifications to some affected companies and trying to get in touch with Amazon, but still no response," Diachenko told Bleeping.
Diachenko also said that most infected servers were on US-based IP addresses. Further, Kromtech is also still analyzing the compiled data to refine the number of infected servers, as 4,000 might not be representative to the niche threat that POS malware is.
As for the two malware strains, AlinaPOS and JackPOS, both are well-known threats. AlinaPOS appeared in late 2012 and spawned the JackPOS variant in 2014.
Both are very popular, are sold on underground hacking forums, and are actively distributed even at this day, years after their initial release.
#JackPos on sell on VXHeaven zzzzz i thought it was leaked?
— Omri Moyal (@GelosSnake) August 18, 2017
http://vxheaven[.]org/forum/viewtopic.php?pid=19761#p19761
ElasticSearch server owners looking into avoiding a disaster by running incorrectly configured server instances can consult the ElasticSearch security guide, available here. A breakdown of the Kromtech findings, along with charts and graphs is available here.
Article updated with new comments from the Kromtech team.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now