Cloud Misconfigurations Spur DB ‘Repatriation’

via Shutterstock
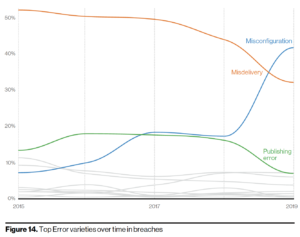
Cloud database misconfigurations are among the fastest growing sources of data breaches over the last five years, according to an annual survey of data breaches.
Those security concerns are among the reasons more enterprise databases are being moved off public clouds, market analysts note.
Overall, Verizon’s latest Data Breach Investigations Report analyzed more than 157,000 incidents, documenting 3,950 confirmed data breaches. Eighty percent of data breaches involved “brute force” hacks or use of lost or stolen credentials. The primary target was web applications and application servers.
The spike in cloud database misconfigurations reflects the steady enterprise embrace of hybrid cloud deployments and the ongoing debate about whether to migrate critical databases to the cloud or keep them in-house. Five years ago, misconfigurations errors hardly registered in the Verizon security survey. Now, they are the fastest growing, up 4.9 percent over the previous year.
“Misconfiguration errors have been increasing,” the Verizon report notes. “This can be, in large part, associated with internet-exposed storage discovered by security researchers and unrelated third parties.”
Added Marco Rottigni, chief technical security officer at cloud security vendor Qualys (NASDAQ: QLYS): “It’s also worth noting that breaches where misconfiguration was leveraged have increased by 4.9 percent from last year and since 2015 there has been a steady growth of this technique.”
A recent breach illustrates the growing problem of configurations errors exposing databases. In 2018, a security researcher discovered a telemedicine database exposed to the Internet via “misconfigured MongoDB instance,” leaving it accessible to anyone without a password.
MongoDB later released new security guidelines and updated its database software with secure default settings via its Atlas service.
Meanwhile, other security surveys also have highlighted cloud misconfigurations. A security report released last fall by McAfee found that fully 99 percent of misconfigurations in the cloud go undetected. On average, McAfee found about 3,500 misconfigurations incidents per month, nearly all of them undiscovered.
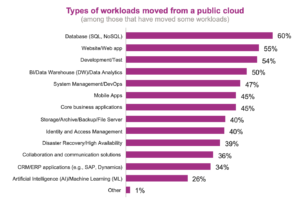
Security concerns figure prominently as reasons why cloud databases are among the workloads most often moved off public clouds. According to IT modernization survey released by IDG Research Services, SQL and NoSQL databases accounted for 60 percent of workloads “repatriated” from public clouds. Overall, the survey found that 84 percent of companies surveyed are moving workloads to on-premise, hosted private clouds or completely out of the cloud.
Along with security, other factors accounting for high repatriation rates were unexpectedly high cloud costs, including data egress charges, and latency issues.
Still, despite the steady migration of other enterprise workloads to the cloud, the Verizon security report found that cloud infrastructure accounted for just 24 percent of data breaches while on-premise assets remained the key target at 70 percent.
There was a sliver of good news in the otherwise sobering data breach survey. Security researchers noted that “fully autonomous artificial hacking intelligence is still at least 15 years away, along with flying cars.”
More details on the Verizon data breach report are here.
Recent items:
Telemedicine Breach Highlights Database Vulnerabilities